LDAP User Store Locate
This WSO2 SOA Enablement Server distribution also contains an LDAP user store. Its implementation class is com.idoox.security.pstore.ldap.LdapUserStore. You must set up this LDAP implementation class using the userstore.impl property. You must also specify additional initialization parameters for LDAP. These can be any parameter specified by the JNDI naming context. For example:
Table 3. LDAP Initialization Parameters
| Parameter | Value |
|---|---|
| java.naming.factory.initial | com.sun.jndi.ldap.LdapCtxFactory |
| java.naming.provider.url | ldap://ldap.foo.org:389 |
| java.naming.security.authentication | simple |
| java.naming.security.principal | cn=Foo Manager,o=foo,c=us |
| java.naming.security.credentials | itscool |
| java.naming.ldap.attributes.binary | userCertificate |
Additional initialization parameters are necessary for WSO2 SOA Enablement Server.
wasp.ldap.searchbase -- The value of this parameter must contain the name of the LDAP context where WSO2 SOA Enablement Server entries are stored. For example o=foo,c=us.
wasp.ldap.userid -- The value of this parameter is the name of the LDAP attribute that contains the user identifier. The default value is uid. Only users that have the attribute specified by this parameter value are managed by WSO2 SOA Enablement Server. You can also set this attribute value to cn.
wasp.ldap.reuseExistingOnly -- If the value of this parameter is false, you can insert or delete users from the LDAP context (given by the wasp.ldap.searchbase parameter value). Otherwise you can only manage WSO2 SOA Enablement Server attributes, such as userPassword and userCertificate. The default is true.
wasp.ldap.defaultcnsuffix -- The LDAP schema typically contains the common name attribute as required. If the wasp.ldap.userid property value is not cn and LDAP user store is configured that it can insert new users (wasp.ldap.reuseExistingOnly property value is not true), the common name attribute is constructed using the value of the user ID suffixed by this string. The default value for this property is an empty string.
wasp.ldap.defaultsn -- The LDAP schema must contain a surname attribute. As the surname attribute is not required by the default WSO2 SOA Enablement Server user store, a surname value must be set when creating a new LDAP subcontext. This property assigns the default value WSO2 SOA Enablement Server as the surname.
To get user store attributes from LDAP, you must add mapping from user store attributes to ldap attributes.
Table 4. User Store → LDAP Attribute Mapping
| User Store Attribute | LDAP Attribute |
|---|---|
| X509Certificate | userCertificate;binary |
X509CertificateChain | userCertificate;binary |
| password | userPassword |
Encrypted passwords We currently support SHA, SSHA, CRYPT, MD5 and SMD5 password digests, as well as plain passwords.
![[Important]](images/important.gif) | Important |
|---|---|
WSO2 SOA Enablement Server for Java tools and the Administration Console always store passwords in plain text. We recommend managing users and their properties (including passwords) with LDAP administrative tools, not SSJ tools. | |
Add the properties in Table 4, “User Store → LDAP Attribute Mapping” to the Protected Store using the GUI Providers Manager tool, as follows:
Configuring LDAP in SSJ
Stop server.
Run the Providers Manager tool:
%WASP_HOME%\bin\ProvidersManager.bat --gui
From the File menu, choose Open File and serverconf.xml.
Click PStore Initialization.
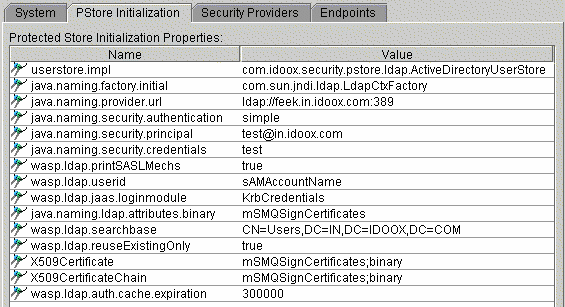
Add the desired properties (for each property, select Add Property from the property menu and fill in the name and value). The properties are listed separately in this chapter for Keystore and User Store, LDAP userstore and Microsoft AD Userstore. A filled-in PStore Initialization form for a Microsoft Active Directory userstore is in Figure 11.
Start server.
![[Note]](images/note.gif) | Note |
|---|---|
For more information on using the ProvidersManager GUI tool, please see The ProvidersManager - GUI Version. | |
![[Important]](images/important.gif) | Important |
|---|---|
You must restart WSO2 SOA Enablement Server for changes to take effect, but first you should modify the WASP_HOME/conf/wasp.policy file to assign administrator privileges to an LDAP user. Use the AuthPolicy tool to modify the WSO2 SOA Enablement Server policy file. | |
![[Important]](images/important.gif) | Important |
|---|---|
Your LDAP schema must be designed to support the following object classes. These classes contain the necessary attributes used by implementation of user store over LDAP.
For more information about directory schemas, please see IBM LDAP Directory Schema. | |
Active Directory User Store Locate
WSO2 SOA Enablement Server can reuse identities from Microsoft Active Directory for authentication and authorization. The implementation class of this UserStore is com.idoox.security.pstore.ldap.ActiveDirectoryUserStore. You must set up this implementation class using the userstore.impl property.
This implementation of User Store can be used only with HttpBasic or SSL security mechanisms. When using HttpBasic, users' passwords are validated by secure authentication (JAAS - Kerberos) to the Active Directory Server. When using WS-Security or SSL, a user's certificate binary is compared with the certificate stored in the Active Directory Server.
Because Microsoft Active Directory is accessed using its LDAP interface, most initialization properties that must be specified to javax.naming.Context are similar to LDAP UserStore. Please see Configuring LDAP in SSJ for directions on setting properties.
Here is a list of the properties that you must set, with example values:
Table 5. LDAP Initialization Parameters for Microsoft Active Directory
| Property | Example Value |
|---|---|
| java.naming.factory.initial | com.sun.jndi.ldap.LdapCtxFactory |
| java.naming.provider.url | ldap://dir.foo.org:389 - Active Directory LDAP url |
| java.naming.security.authentication | simple |
| java.naming.security.principal | wasp@foo.org - identity name in Active Directory with permission to get list of users from directory |
| java.naming.security.credentials | its password |
| java.naming.ldap.attributes.binary | mSMQSignCertificates - handle this attribute binary |
To get user store attributes from the directory you must add mapping from user store attributes to LDAP attributes.
Table 6. User Store → LDAP Attribute Mapping for Microsoft Active Directory
| User Store attribute | LDAP Attribute |
|---|---|
| X509Certificate | mSMQSignCertificates;binary |
| X509CertificateChain | mSMQSignCertificates;binary |
Table 7. Additional User Store Initialization Parameters
| User Store attribute | Value | Function |
|---|---|---|
| wasp.ldap.jaas.loginmodule | KrbCredentials | Specifies that UserStore uses Kerberos JAAS login module for authentication to directory. (See System Requirements for Kerberos at Sun's Kerberos Requirements page.) If this property is not specified, UserStore uses simple authentication (which, among other things, means that the password can be sniffed). |
wasp.ldap.searchbase | CN=Users,DC=FOO,DC=COM | Search base for users in directory |
| wasp.ldap.userid | sAMAccountName | name of directory attribute that holds identity name |
| wasp.ldap.reuseExistingOnly | true | Specifies that directory is used in read-only mode. You cannot add/remove/modify directory users from WSO2 SOA Enablement Server. |
| wasp.ldap.auth.cache.expiration | 300000 | After successful authentication, users' credentials are stored in cache. Expiration of this cache time can be specified in milliseconds using this property (default expiration time is 300000). |
To set up Microsoft Active Directory as a WSO2 SOA Enablement Server Users Store, follow the protected store setup instructions in Configuring LDAP in SSJ.